
Data Authentication
Date: 06/2021
With the help of the ETS, users can retrieve personal and individual pension data. Therefore, the institution providing the data must be certain that the person requesting the data is who he or she claims to be, meaning the user must be identified and authenticated. This is a particular challenge for the ETS, as different countries have to be covered.
1. Digital identity
A digital identity is something that a person presents to prove “this is who I am”.
There are different ways to create an identity. The way of creation determine the level of reliability of the identity (LoR).
| Level of reliability (LoR) | Key features | Exemple |
| Low | Self-asserted identity. No verification, validation of evidence. Limited degree of confidence in the claimed or asserted identity of a Person. | Username |
| Substantial | Remote or in-person identity proofing. Substantial degree of confidence in the claimed or asserted identity of a Person. | Digital ID via remote |
| High | In-person identity proofing. Higher degree of confidence in the claimed or asserted identity of a Person. | Smart card or digital ID in-person. |
2. User authentication factors
User authentication factors is presenting 1 or more pieces of evidence related to a digital identity. There are different authentication factors:
| Authentication factor | Exemples |
| Something you know | Password, OneTimePassword (OTP),... |
| Something you have | ID card,... |
| Something you are | Unique biometric features such as fingerprint |
| Single factor authentication (SFA) | Something you know, have, are... The most basic SFA is a password = "something you know". |
| Multiple factor authentication (MFA) | At least 2 authentication factors (same of different). 2FA = two factor authentication = password + OneTimePassword (OTP) = 2 times "something your know". 2FA = two factor authentication = ID card + PIN = "something you have" + "something your know" |
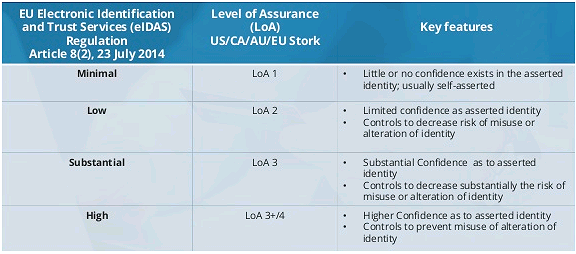
3. Level of Assurance (LoA)
The level of assurance (LoA) needed for the digital key is based on the consequence of authentication errors and/or misuse of credentials.
Assurance answers the question, “How sure am I that you are who you say you are?”. In other words, how much confidence does a relying party have that the digital identity presented is in the possession of the person whose identity is being asserted.
| Level of Assurance (LoA) | Description |
| Low | At least 1 authentication factor |
| Substantial | At least 2 authentication factors |
| High | At least 2 different authentication factors |
4. Digital key
A digital key exists of a digital identity in combination with authentication factors.
It is possible to create digital keys with different level of assurance LoA.
The most basic form of a digital key is user ID and password (SFA). The Level of Assurance (LoA) of this digital key is low.
The security can be increased by increasing the number of authentication factors, like adding another “something you know” factor such as OneTimePassword (OTP) or “something you own” factor such as an ID Card or “something you are” factor as unique biometric features such as fingerprint. These multiple factor authentications (MFA) increase the LoA to substantial and high.
eIDAS
eIDAS is a digital key that gives access to an account. With eIDAS an European citizen can utilize his/her national digital key to get access to an account in another European country. Behind eIDAS there are different digital keys with different LoA.
Digital keys distributed by national authorities are validated digital keys. So there is a higher confidence that the personal data behind the digital identity belongs the physical person behind the key.
5. Account
Creating an account makes it possible that users have control over their information.
To create an account or to get access to your account, you need a digital key.
The digital identity used by the citizen determines the LoR of the account.
An account can be created by the citizen by putting in an username, password and other personal data such as email, name, first name, sex, address, birth date, … (= digital identity with LoR low). These data are entered by the user and are not verified information. These data related to the account are categorized with a low level of reliability (LoR).
To increase the LoR it’s necessary to use verified information of the user (identity proofing). This can be done by using a digital identity with LoR substantial or high of the citizen who wants to create an account. The data associated (name, first name, sex, …) with the digital identity are categorized with substantial or high LoR. So when creating an account with these personal data there is more confidence that these data belong to the physical person behind the digital key/indentity.
To get access to privacy related data it’s advisable to require a digital key with LoA substantial or high.
6. Authentication
Authentication is the process of recognizing a user’s identity who wants to have access to an account, a device, website, tool, data, … Telling who you are and prove you are who you are.
Authentication is using a digital key or presenting your digital ID and authentication factors to get access to an account, ….
7. FindYourPension
In FindYourPension there are two possibilities for creating an account.
Website
A citizen can create an account and store/consult data. The account is created with userID (digital identity has a low LoR) and password together with OTP (authentication LoA is substantial).
The citizen can add personal and pension data to this account. The data added by the citizen has a low LoR because there is no validation process of the added data.

Getting data from external resource servers
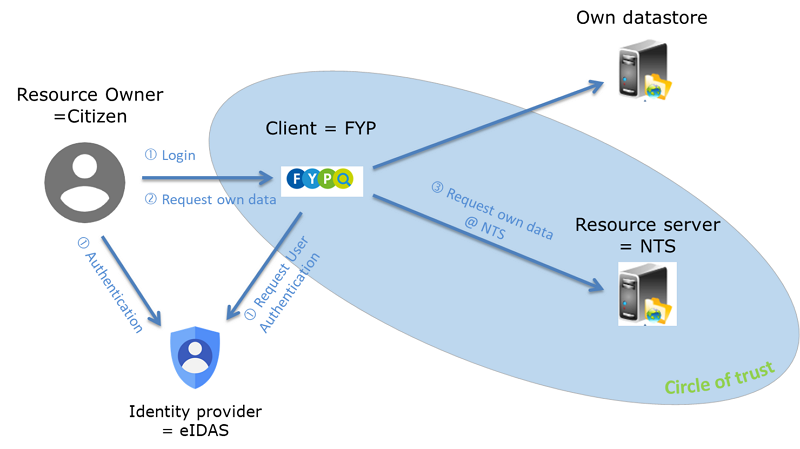
In FindYourPension the citizen can ask to get the pension data stored in different NTS. In this case it is not only important to have an appropriate LoA for the authentication (required LoA defined by the NTS) but it is also important to be sure that only the resource owner can get access to the data stored in different NTS. The digital identity must be with a LoR substantial or high and the LoA must also be substantial or high.
Be using eIDAS as identity provider we can define that the minimum LoA of the used digital key is substantial or high. That means that the digital identity had a validation process and there is a higher degree of certainty.
Beside authentication is identification of the citizen (resource owner) by the NTS (resource server) important. Identification is matching the identity of the user with the administrative identity at the datasource (NTS). This identification of the citizen by the NTS can best be done by using the personal data (with LoR high) coming from the used digital key. In this way the NTS has the responsibility that only the authenticated citizen gets his/her own pension data.
Identification of the citizen via personal data can be a problem for the NTS. In that case the NTS can ask the ID of the citizen known by that NTS. The NTS must do a coherence check to be sure that ID belongs to the physical person behind the digital key (coherence check of the personal data associated with the verified digital identity and the personal data associated with the given ID in the datasource (NTS)). Otherwise everyone can ask the pension data from everyone from who the ID is known.
8. Sources
https://id4d.worldbank.org/guide/credentials-authentication
https://www.aeteurope.com/news/strong-authentication/